Organizations of all sizes become victims of cyber attacks because they lack proven, repeatable ways to secure their environment at the foundational level before something goes wrong.
In other words, "discover" and "mitigate" or "remediate", or "auto-remediate" simply does not work.
💥Security is often failing through a gap between what’s expected and written down and what actually gets implemented in the environment.
- Most organizations have security policies.
- Many organizations have compliance automation tools to comply with regulations and laws.
- But few have confidence that the infrastructure is actually configured the way the policies require.
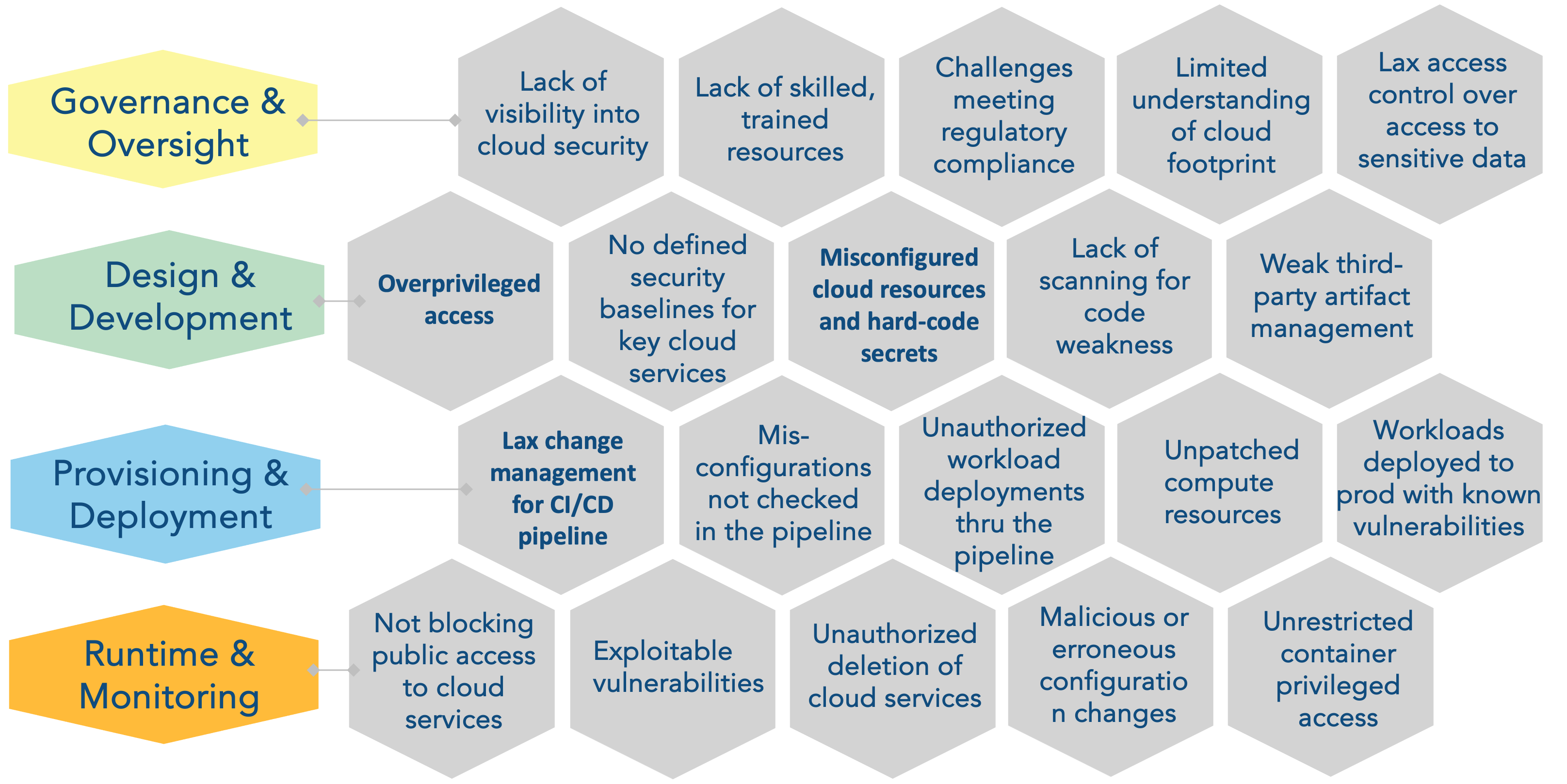
Large number of breaches are caused by preventable misconfigurations. And the root cause? Dev teams are moving fast but are not security experts — and guardrails are not embedded by default.
The Security Execution Gap
This often happens because Dev and IT teams aren’t consistently implementing what policies require creating a security implementation and deployment gap. And that gap? It’s expensive — costing companies time, credibility, and millions in risk.
⚠️ What’s typically going wrong in the real world:
- Misconfigured cloud services → Risk of breaches, failed audits, brand damage.
- Governments are creating more complex regulatory mandates, to solve for security, with high penalties and fines for non-compliance → Growing GRC headcount, while not improving security posture.
- Ad hoc practices across Dev and IT teams, overwhelming security → Inconsistent controls, reinvented for every project.
- DevOps, IT, Security misaligned → Slower delivery, creating control gaps.
- Security policies exist on paper or in GRC tool only → No enforcement in actual infrastructure or workloads.
- Security posture tools generate huge amount of false-positive or irrelevant findings → Dev teams are overloaded and often ignore tickets.
How do we fix this?
It’s well known that fixing software bugs in production costs 100x more than during development.
Why wait for CNAPP tools to flag a misconfiguration you can prevent by having guardrails set in your CI/CD pipeline?
Before the cloud era, security architects defined and documented functional and non-functional requirements tailored to the risk profile of the application — and validated them before go-live. We can do the same today — with a modern, scalable approach.
🛠 Solution: effective security governance starting with foundation and built-in execution
- 🚫 We don’t need more dashboards.
- ✅ We need security foundation that guides infrastructure and workloads from day one.
💡 What this looks like:
- Prescriptive configuration baselines tailored to company standards and aligned to government regulations
- Preventive guardrails and detective validation checks embedded into the CI/CD pipeline
- Runbooks with step-by-step operational guidance
- Validation checks that demonstrate compliance before auditors ask
- Integration with existing AI, CNAPP or compliance tools
The business outcome:
- ✅ Consistent security practices across teams.
- ✅ Standardization reducing operational risk.
- ✅ Improved Dev teams productivity with less time wasted on ad hoc security tasks.
- ✅ Reduced CISO legal liability through proof of due care.
- ✅ Minimized efforts to demonstrate regulatory compliance with real-time proof of effective control enforcement and audit automation.
- ✅Transformed security into a business enabler — not just a cost center.